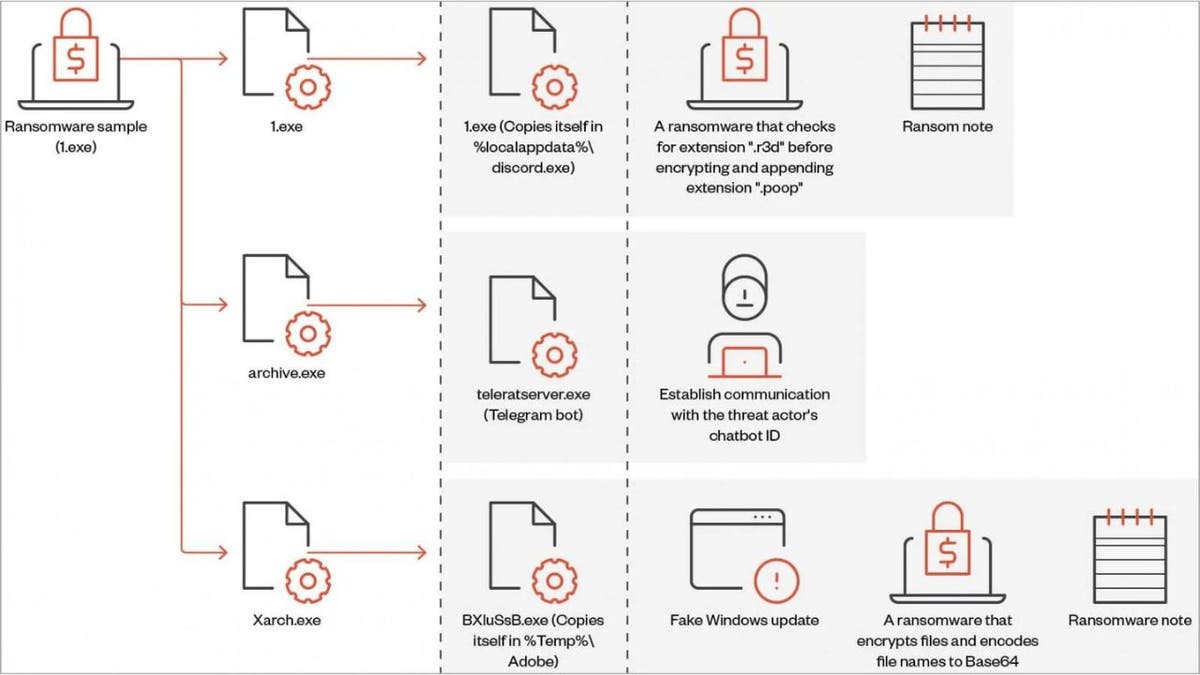
Connecting to websites and apps using your Google account is undeniably convenient. However, this ease of access comes with potential risks to your digital security. It's crucial to understand the implications of granting third-party apps access to your Google data and take proactive steps to protect your information.
When you choose the "Sign in with Google" option, you're essentially giving the app permission to view and potentially utilize specific information from your Google account. This convenience can streamline your experience by integrating app functionalities with Google services, but it also requires a degree of trust in the third-party app.
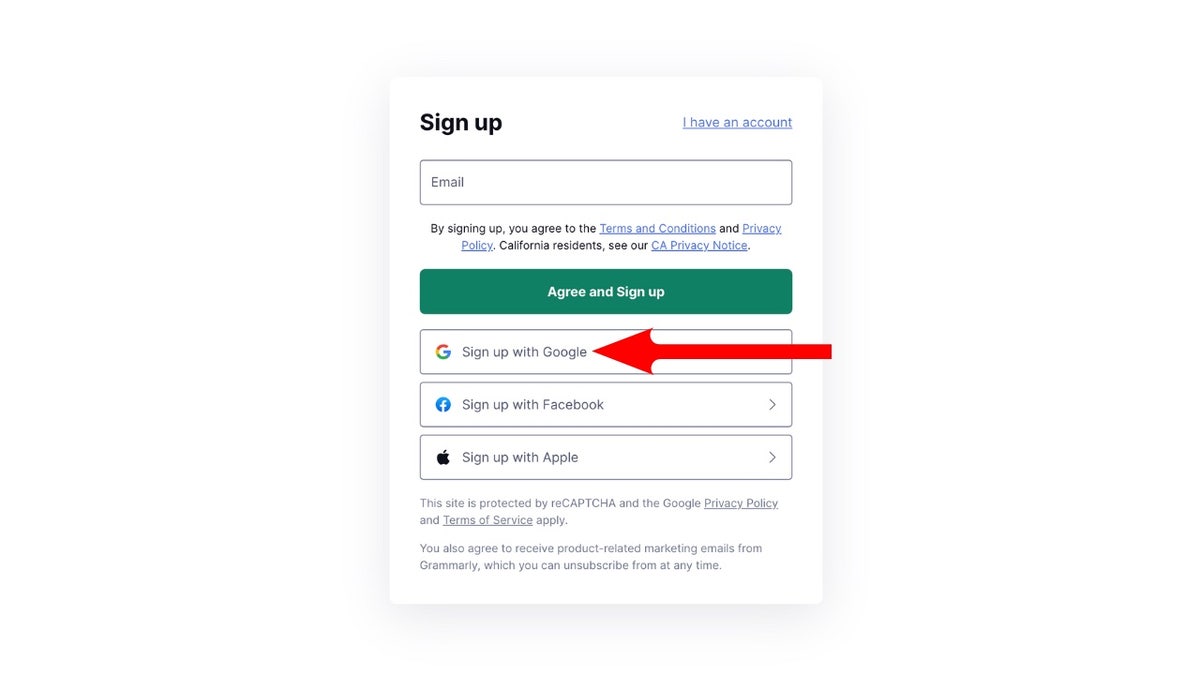
Before connecting any app to your Google account, it's essential to assess the developer's credibility. Look for contact information, a physical address, and a comprehensive privacy policy on the app's website or Google Play Store page. Absence of this information is a significant red flag.
User reviews can offer valuable insights into an app's trustworthiness. Check reviews on app stores and perform online searches to gauge user experiences. While reviews can be subjective, they often highlight potential security or privacy concerns.
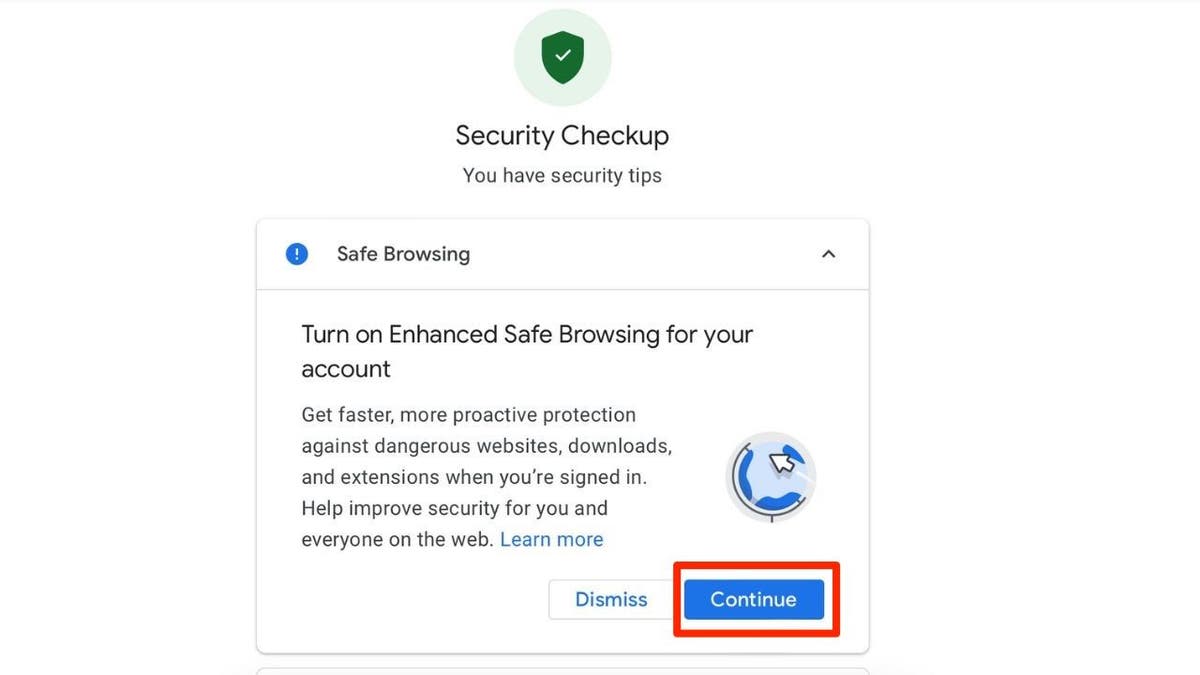
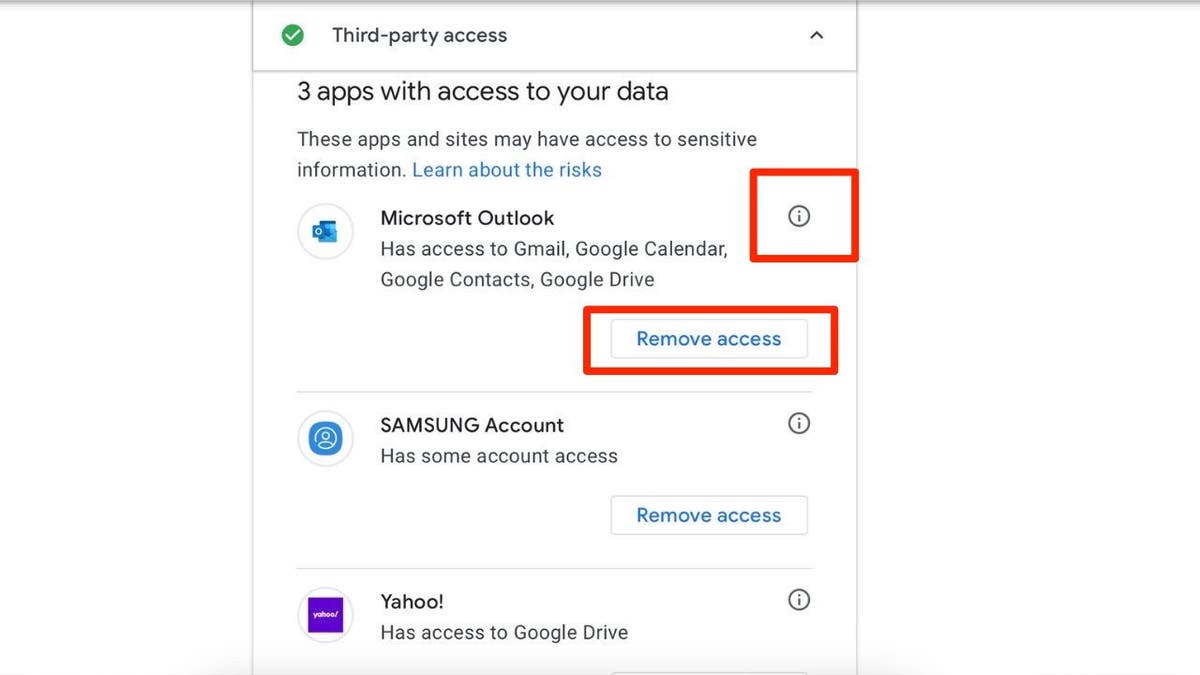
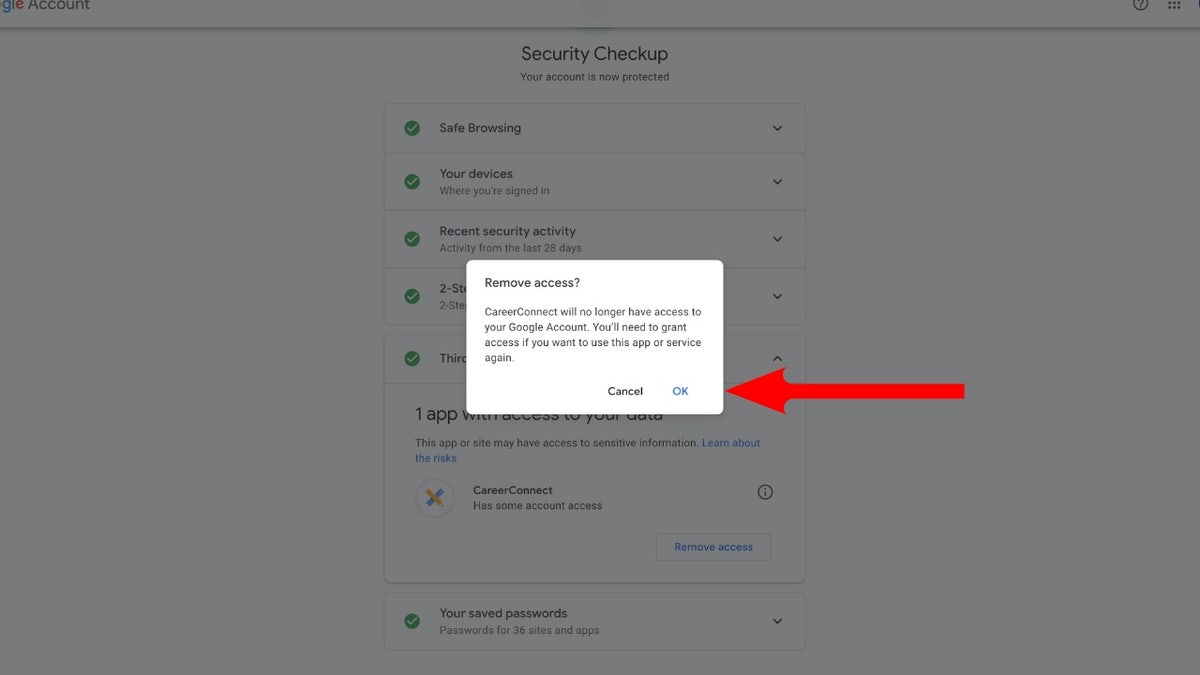
Google provides a valuable tool called Security Checkup that empowers you to manage and control app permissions. Access this feature through your Google account settings to identify potential risks and revoke access from apps you no longer trust or use.
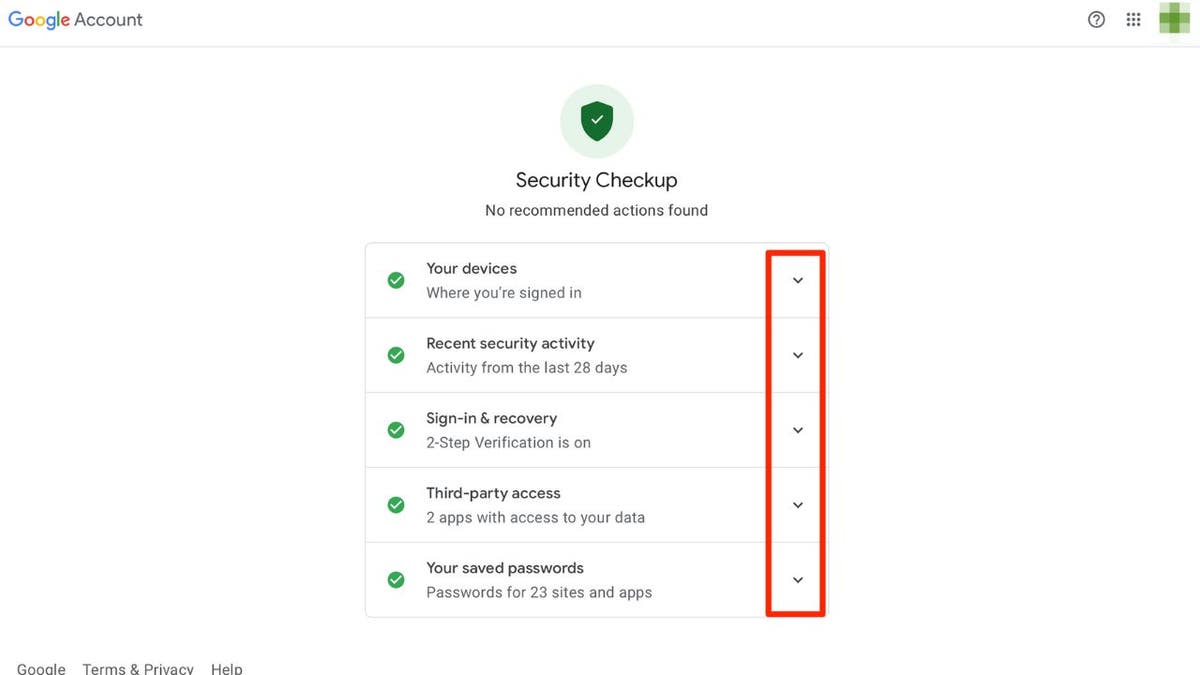
Within the Security Checkup, you can:
- Enable Enhanced Safe Browsing for proactive protection against malicious websites and downloads.
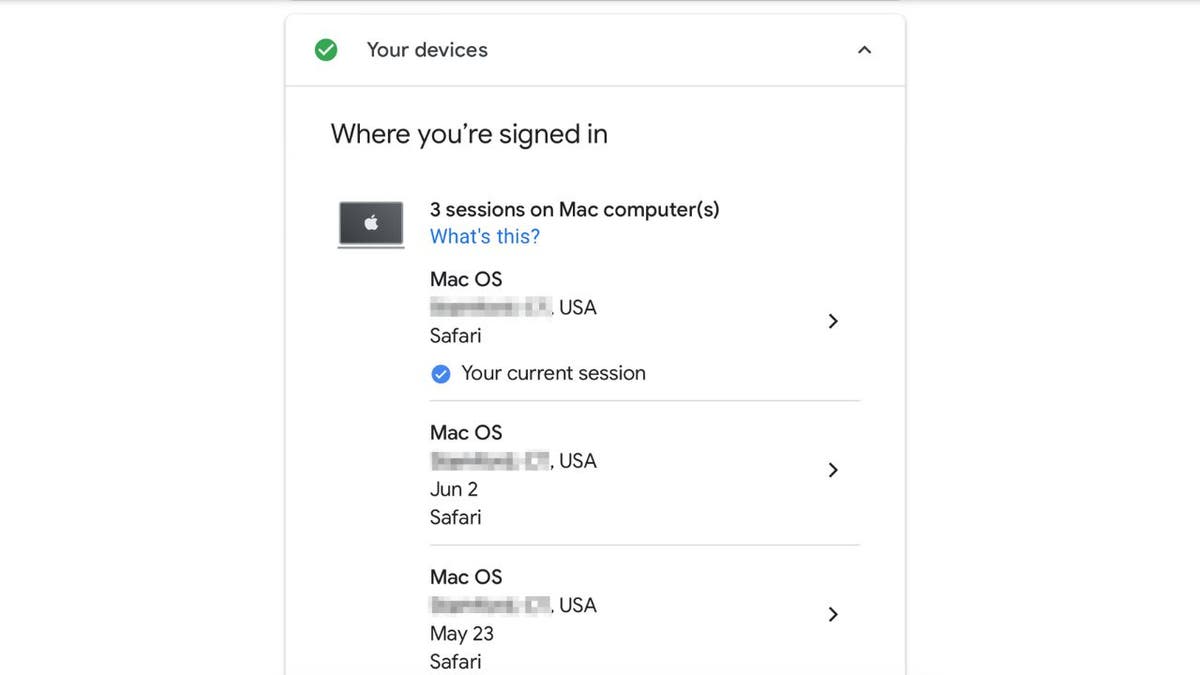
- Review devices connected to your account and sign out of any unfamiliar ones.
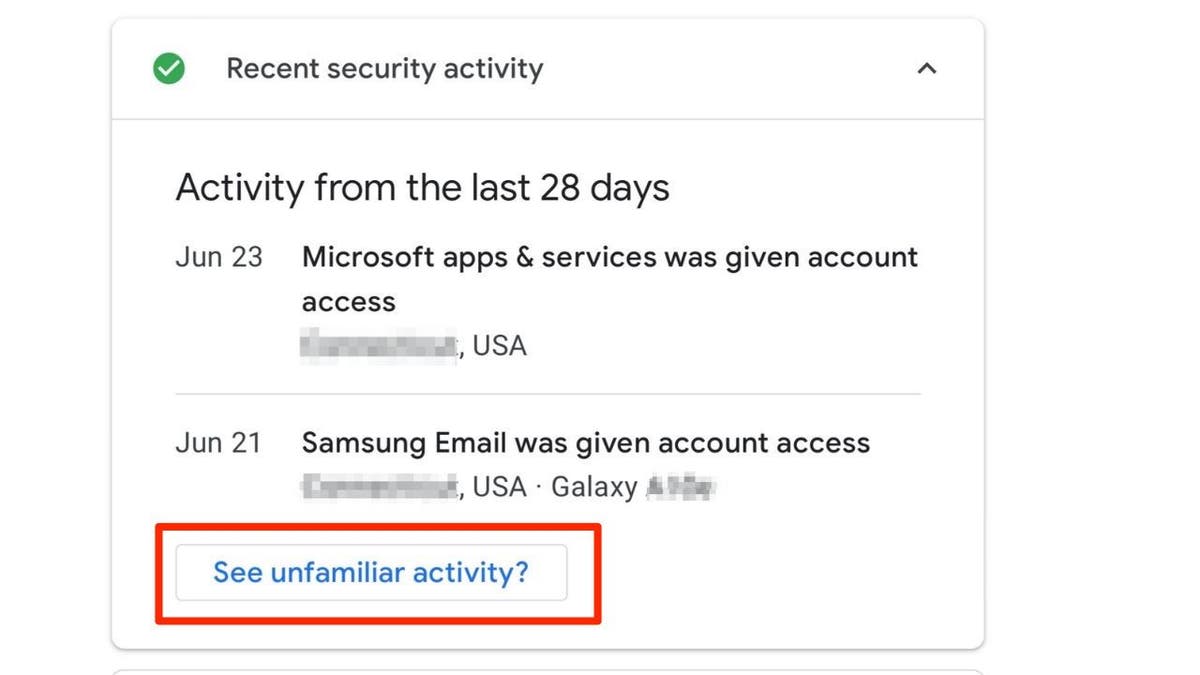
- Monitor recent security activity and change your password if you detect suspicious actions.
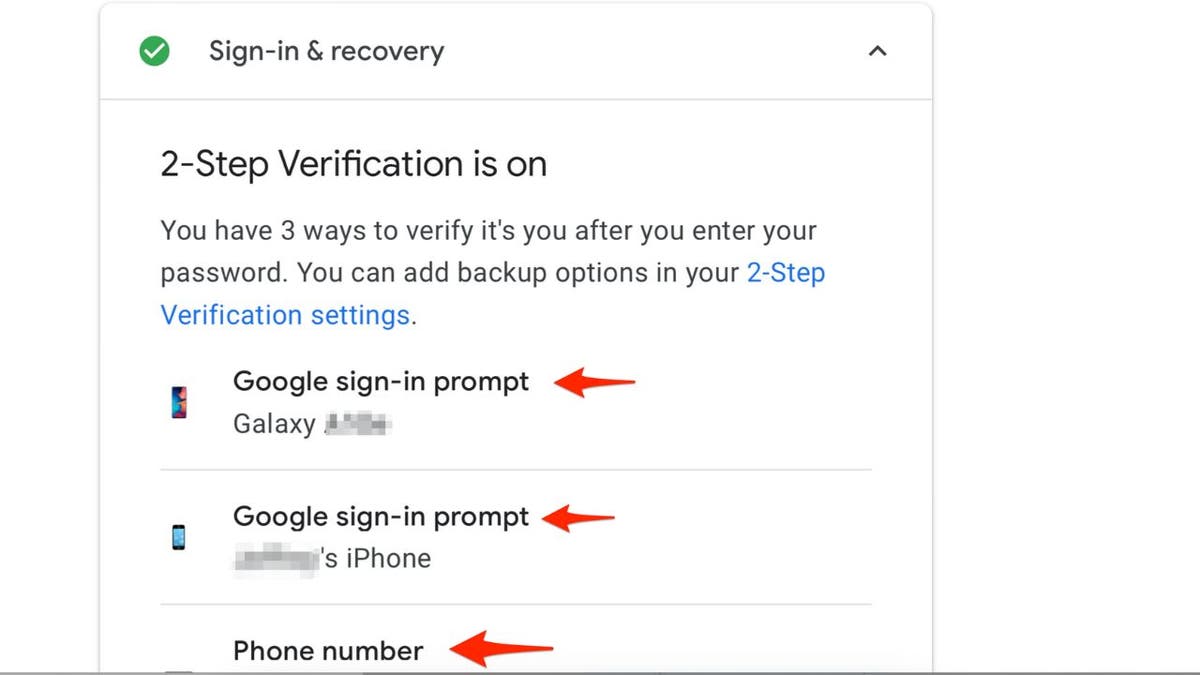
- Strengthen your account security with two-factor authentication.
- Manage third-party app access and revoke permissions for apps you no longer use or trust.
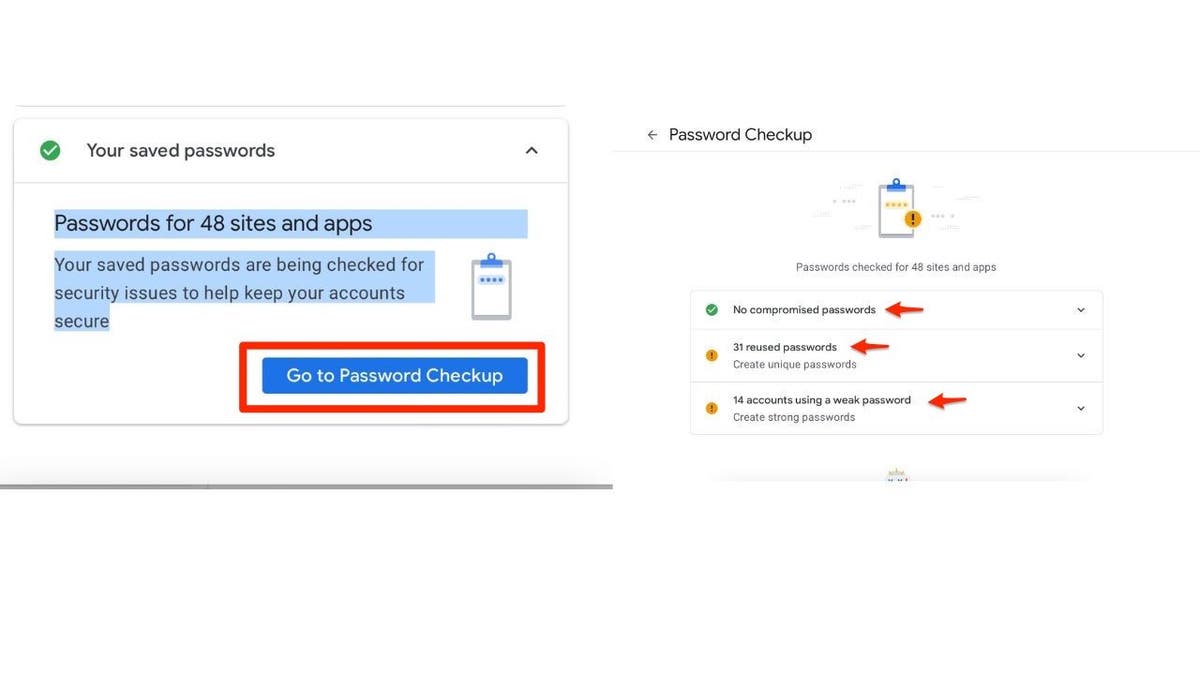
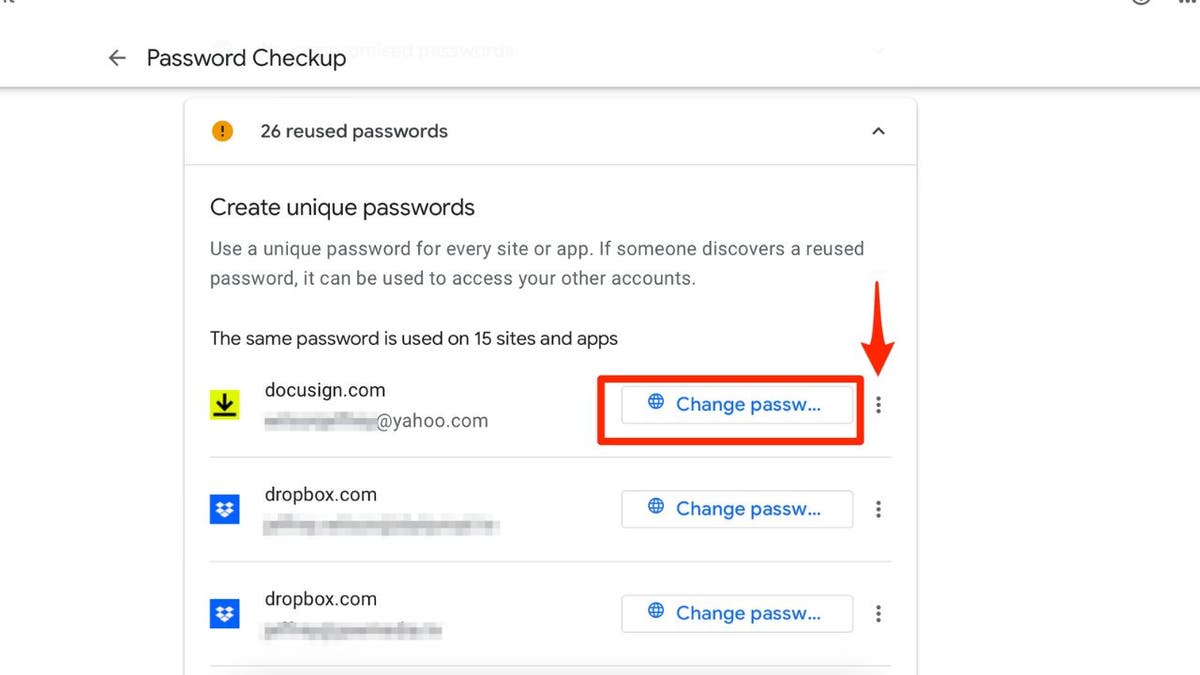
- Review and update saved passwords to enhance your overall online security.